Sandbox is an option (--option) you can pass to nix-build and other commands, it exists on:
- Nix 2.3 (stable)
- Nix 2.4 (unstable)
- Nix 2.4 (unstable) with Flakes support (a.k.a. passing
--experimental-features flakes) (Sometimes they call this Nix 3.0)
Sandbox is pretty much the core reason why Nix is so awesome. Sandbox allows you to build derivations in an empty file system, without access to the internet, and on a perfectly empty environment, so pretty much it ensures the build step is a pure function without side effects or visibility to the outside world
According to the Nix manual:
The default is
trueon Linux andfalseon all other platforms.
The link you sent, is for nixpkgs, not nix. Sandbox is a feature of Nix, that is disabled/enabled on Nixpkgs for achieving pure builds
Could you tell more about why disabling sandboxing was necessary?
It was not necessary, but it was very convenient back then
Let’s start from the context that our first iteration was migrating from Docker to writing “bash scripts with dependencies provided by nix-shell”. On our next iteration we wanted to benefit from the cacheability of nix-build, but we found it very hard to make our existing packaging run on a restricted environment with the sandbox. (How to do a pip/npm/ruby-gem install if you don’t have access to the internet). So we decided to use nix-build --option sandbox false --option restrict-eval false in order to grant internet access to derivations, and benefit from the nix-build cache at the trade-off of not being perfectly pure
So again, it was not necessary to disable sandbox, it was just convenient not to spend too much time and effort being perfectly pure. At this point the benefits of using nix-build instead of nix-shell were far greater. Besides code running on nix-builds with sandbox disabled is also more pure than nix-shell, so this was a victory in our context
Wouldn’t it have prevented the build bugs?
No, the bug was directly on the Nix binary and not related to our code, see why:
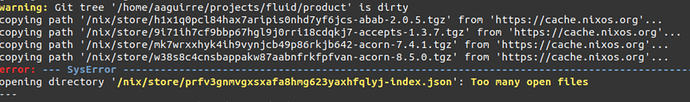
This is the exact image of the bug:
file descriptors are finite, here it seems that either Nix is leaking them, or there is no control that avoids opening more than X
This happened on Nix 2.4 (unstable) with flakes support. When building the same from Nix 2.3 (stable) the error did not happen. So this is one of the strong reasons why we downgraded to Nix 2.3 (stable). Stable normally means code has passed through more tests and real usage and more bugs were identified and fixed. You normally want stability on production systems