Hello NixOS folks! ![]()
I’m stuck and need your help… I’d like to know if :
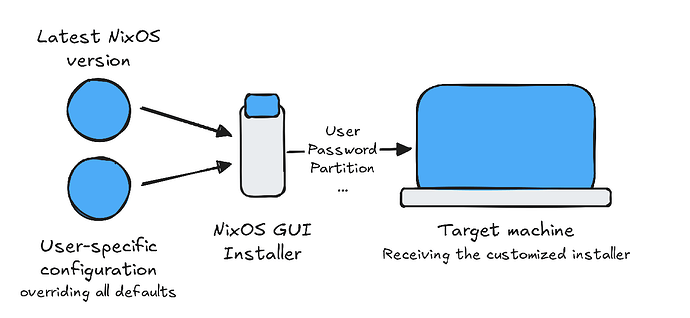
- It’s possible to edit the defaults of the NixOS installer? For me to package all my required apps along their configurations, as well as desktop environment configuration.
- Can it be packaged into an ISO (not a live OS, one that you can install on the target machine)
I was thinking that the installer (e.g. Calamares) would be used for the basic setup, including user, password, partitioning, as it is today. And the next step would automatically read your user-specific configuration (e.g. multi-file configuration.nix) and apply it. Afterwards, restart, login and tadaa ![]()
Right after the installation, you’ll get your customized NixOS. No need to run extra commands, or fetching your configurations somewhere else.
I’ve already built several ISO (vm images + standard .iso) and tested them with QEMU, but haven’t found a way to automatically apply my custom configuration which I import in the ISO file (e.g. iso.nix).
I’ve been using nixos-generate and nix-build :
nix-shell -p nixos-generators --run "nixos-generate --format iso --configuration ./iso.nix -o result"nix-shell -p nixos-generators --run "nixos-generate --format vm --configuration ./iso.nix -o result"nix-build '<nixpkgs/nixos>' -A vm -I nixpkgs=channel:nixos-24.11 -I nixos-config=./iso.nix
I’m currently running :
- NixOS
- with Gnome
- on ext4 + LUKS
- with the configuration (split into multiple files) which is the one I’d like to package
Related threads that I’ve already checked, but haven’t understood all the steps yet (which ones are automatic/manual) :
- Reddit - Heart of the internet
- Customize configuration.nix created by installer
- Install NixOS with an existing configuration
- dotfiles/NOTES.md at aa6f128b36a159ce43d8abea515c918f05bd6600 · acobster/dotfiles · GitHub
Thanks in advance for your inputs ![]()
PS: Cross-posted on Reddit