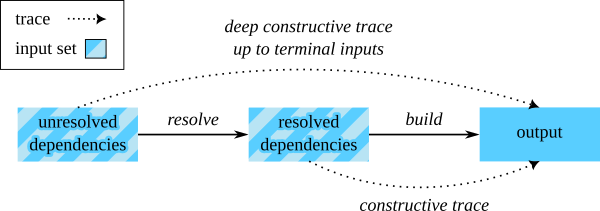
I have analyzed how cloud build systems, like Nix, work in terms of trust, and came up with the following diagram:
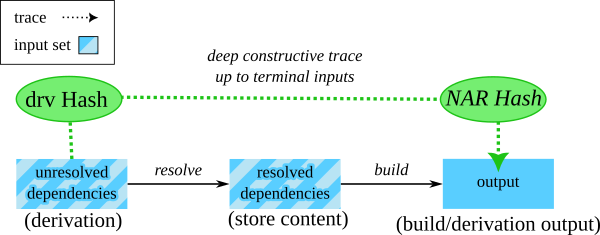
If we look at input addressed derivations in Nix from this perspective we get the following diagram, with the green part of it forming a deep constructive trace up to terminal inputs.
Each individual trace, from derivation hash to NAR hash, is what we sign in order to establish trust in signed outputs.
I would also like to analyze content addressed Nix in the same way, but there, we have two signed data structures, so two arrows:
- derivations
- realizations (as far as I can tell caches do not actually implement the endpoints to share those)
For both data structures it is unclear to me which pairs of hashes they sign (in order to state that relationship is trustworthy according to the signer).
Is there anyone who can help me with this?
PS: the first graphic and general analysis is from my paper that I posted about in Extending cloud build systems to eliminate transitive trust.
If I can I would like to find these things out for my NixCon talks.