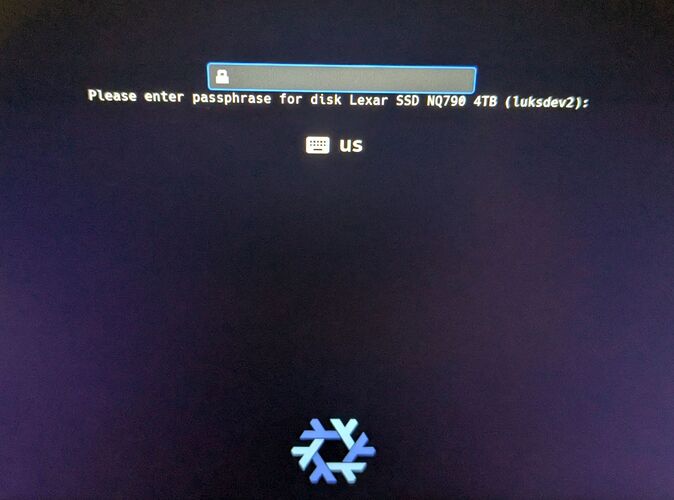
Linux systems show a lot of useful info when booting. On NixOS this is the default. The LUKS password entry finishes “Stage 1”, in “Stage 2” the unlocked system is booted.
All of this is shown in text only, which works fine, is efficient and simple, but might not suit your taste.
Fedora and other distributions primarily show a graphical boot screen, only when pressing Esc you see the text output.
We can achieve the same with a small config.
Note
If you use LUKS encryption with a keyfile, read below on how to make this work.
There also seems to be a bug where the password screen disappears when waiting for some time, requiring a reboot.
Needed Changes
But NixOS has quite some defaults set, but you need to change some configs to enable it fully.
- prevent some information from being displayed
- enable systemd in an early stage
- enable the plymouth boot screen
Optionally you can use a custom theme, logo, font and more.
Configuration
To keep things clean, you can create a /etc/nixos/configuration/boot.nix file and import it in your configuration.nix. In there you can set
{ config, lib, pkgs, ... }:
{
boot = {
# silence first boot output
consoleLogLevel = 3;
initrd.verbose = false;
initrd.systemd.enable = true;
kernelParams = [
"quiet"
"splash"
"intremap=on"
"boot.shell_on_fail"
"udev.log_priority=3"
"rd.systemd.show_status=auto"
];
# plymouth, showing after LUKS unlock
plymouth.enable = true;
plymouth.font = "${pkgs.hack-font}/share/fonts/truetype/Hack-Regular.ttf";
plymouth.logo = "${pkgs.nixos-icons}/share/icons/hicolor/128x128/apps/nix-snowflake.png";
};
}
Font and logo are optional, by default a white NixOS snowflake is used.
You can also set a custom theme, but this can be more complex. As motivation, have a look at this repo