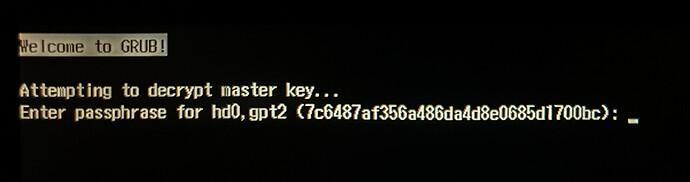
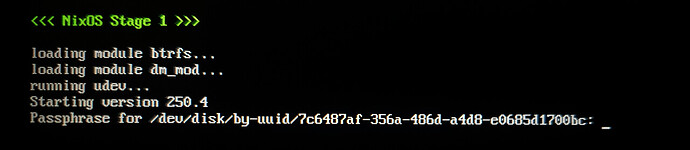
Hi, how should I properly configure my full disk encryption system to unlock it with a single password input? Now it asks me to enter my password twice.
I have one drive that I separated like so:
NAME FSTYPE FSVER LABEL UUID FSAVAIL FSUSE% MOUNTPOINTS
nvme0n1
├─nvme0n1p1 vfat FAT32 11CD-4829 510.6M 0% /boot/efi
└─nvme0n1p2 crypto_LUKS 1 7c6487af-356a-486d-a4d8-e0685d1700bc
└─crypted-root btrfs root 33ecc27d-9185-412c-93ab-e8c983498390 367.2G 23% /swap
/home
/.snapshots
/nix/store
/nix
/
My configuration file:
boot = {
loader = {
efi = {
canTouchEfiVariables = true;
efiSysMountPoint = "/boot/efi";
};
grub = {
enable = true;
device = "nodev";
version = 2;
efiSupport = true;
enableCryptodisk = true;
};
};
initrd = {
luks.devices.root = {
device = "/dev/disk/by-uuid/7c6487af-356a-486d-a4d8-e0685d1700bc";
preLVM = true;
keyFile = "/keyfile.bin";
allowDiscards = true;
};
secrets = {
"keyfile.bin" = "/etc/secrets/initrd/keyfile.bin";
};
};
};