.
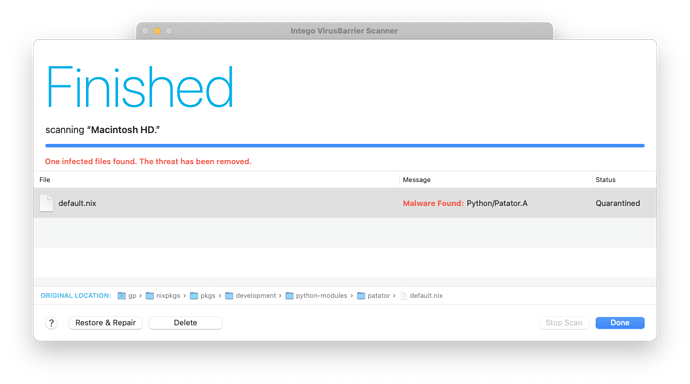
…/python-modules/patator/default.nix
I do not quite understand, what exactly do you want to tell us with this post?
It’s (probably?) a hacking tool: GitHub - lanjelot/patator: Patator is a multi-purpose brute-forcer, with a modular design and a flexible usage.. Some virusscanners flag those as viruses/(which is defensible, but can be annoying).
Not in this case though, since it’s flagging the nix expression used to build the package, instead of the tool itself. The expression doesn’t contain anything other than the tool’s name and a two word description (which is also part of the tool itself).
The AV signature is bogus.
Yes, that’s bad. Sometimes it flags on urls, but an expression like this should not be flagged.
Thought I’d share some info on this old post as I came across it after running into this issue myself recently when installingflox v1.3.3.
Vitals:
- macOS v13.7
- VirusBarrier v10.9.94 (malware defs from 2024-10-03)
How to Reproduce:
Problem reproduces as seen below with the default.nix file getting quarantined as Python/Patator.A during step 3.
- removed the
default.nixfile from quarantine - removed flox
brew uninstall flox - installed flox
brew install flox
Workaround:
In the Intego VirusBarrier settings, there is a selection under the Scanner tab to toggle on/off detecting “Hacking Tools” and a few other categories of potential malware.
When I disabled the detection of “Hacking Tools” and re-executed the steps above, the default.nix file was no longer quarantined.
Intego has now updated malware definitions to no longer quarantine the default.nix file as of the Oct 8, 2004 definitions update.
Intego VirusBarrier Version 10.9.94 (3649) – malware definitions v2024-10-08