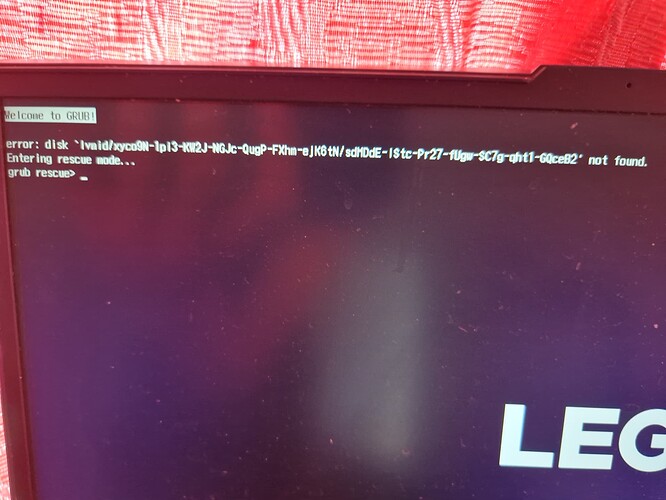
i need help
after updating my bootloader config to make add removable option im having issue booting up. When my os boots into bootloader it straight away shows error saying lvmid/random_uuid not found and goes to grub rescue. Matter of fact here is a picture of the error
I have made such everything is in right place whatever im pretty sure. Im running nixos off external ssd for context and my system is UEFI
lsblk view for my filesystem and uuids
[root@nixos:~]# lsblk -f
NAME FSTYPE FSVER LABEL UUID FSAVAIL FSUSE% MOUNTPOINTS
loop0 squashfs 4.0 0 100% /nix/.ro-store
sda
├─sda1 vfat FAT32 BOOTLOADER BAEB-E6A9 333.4M 33% /mnt/boot/efi
└─sda2 crypto_LUKS 2 abb0bf28-ff6b-441c-aa12-2a678b8ca042
└─cryptroot LVM2_member LVM2 001 GpW1at-btt5-hPxj-WoqJ-lSjR-QEM7-oIu6Nl
├─vg-swap swap 1 SWAP 38a476a4-62fa-496e-8f62-56624447d1fd [SWAP]
└─vg-root f2fs 1.14 ROOT 745b5250-fc07-472a-ad81-af17316e649d 772.3G 14% /mnt
sdb
├─sdb1 exfat 1.0 Ventoy 9CA0-AE2F
│ └─ventoy iso9660 Joliet Extension nixos-gnome-22.05-x86_64 1980-01-01-00-00-00-00 0 100% /iso
└─sdb2 vfat FAT16 VTOYEFI 0922-588F
Settings for luks and grub in my configuration.nix
# Use the systemd-boot EFI boot loader.
#boot.loader.systemd-boot.enable = true;
boot.initrd.luks.devices = {
cryptroot = {
device = "/dev/disk/by-uuid/abb0bf28-ff6b-441c-aa12-2a678b8ca042";
preLVM = true;
allowDiscards = true;
};
};
boot.loader = {
efi = {
canTouchEfiVariables = false;
efiSysMountPoint = "/boot/efi";
};
grub = {
enable = true;
version = 2;
efiSupport = true;
efiInstallAsRemovable = true;
enableCryptodisk = true;
device = "nodev";
};
};
And lastly my hardware configuration.nix filesystems config
fileSystems."/" =
{ device = "/dev/disk/by-uuid/745b5250-fc07-472a-ad81-af17316e649d";
fsType = "f2fs";
};
fileSystems."/boot/efi" =
{ device = "/dev/disk/by-uuid/BAEB-E6A9";
fsType = "vfat";
};
swapDevices =
[ { device = "/dev/disk/by-uuid/38a476a4-62fa-496e-8f62-56624447d1fd"; }
];