TLDR:
- Supply Chain Security has reached critical mind-share
- Nix solves or can solve many Supply Chain Security problems
- The nix community has broad knowledge going back over 10 years that can really impact the direction of discussion around dependencies and reproducibility etc
- Where is nix’s funding tho?.. /s
- But seriously, we need to consider why nix isn’t receiving funding and how we can fix that
- This is a massive opportunity for nix growth among users and the industry, and for funding to both the nix projects and individuals
- Getting involved = Getting nix funding
- Getting involved = Getting nix adoption
It would suck for big industry to waltz up and trample on the awesome work done by the nix community over such long period. Now is when the nix community can make it’s mark and display it’s hard work; delay and the opportunity will pass us by.
This is also a general plea to the community to express interest when people reach out an olive branch. There was an opportunity to be put forward for a pro-bono security audit but it received very little response. People will eventually stop bothering to reach out, which would suck.
And just to clarify I’m not suggesting nix become corporate, just seeing wider usage and appreciation for the work done around nix would be great.
If any of that sounds good please read the whole post
Supply Chain Security is all about understanding all of your software dependencies from top to bottom.
You may have noticed nix (and it’s associated projects) have been tackling this for over 10 years!
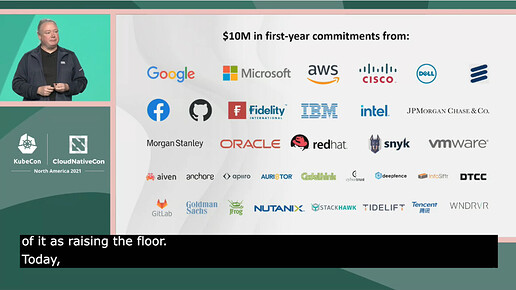
There is a massive increase in interest around Supply Chain Security in industry due to massive compromises month after month. As the title states, there’s $10 million donated to the Open Source Security Foundation in the first year alone
Supply-chain Levels for Software Artifacts or SLSA is a framework for Supply Chain Security, currently in development.
It’s not perfect but that’s exactly why it’s important we get involved. This is the opportunity for the lessons from nix to help SLSA avoid pitfalls.
@mlieberman85 is the chief architect of that CNCF secure supply chain project and on the board for SLSA and joshuagl/Joshua Lock from VMWare who’s also doing a lot of work on SLSA and interested in Nix.
We have opened an unofficial Nix + SLSA matrix channel to discuss the topic of SLSA, how nix fits in, and what issues SLSA has etc (e.g. I think reproducibility is a lot more important than just a suggested requirement at the highest “SLSA level”)
To get involved read the get involved page and/or follow the GitHub issues that power the development of the framework
Google has committed $10 billion (with a B) to cyber security, $100 million of that “to support third-party foundations that manage open source security priorities and help fix vulnerabilities”
$1 million has gone to the Linux Foundation for the Secure Open Source Rewards program offering funding to people who implement security improvements such as SLSA
https://sos.dev/
Reward amounts are determined based on complexity and impact of work:
| Amount | Nature of improvement |
|---|---|
| $10,000 or more | Complicated, high-impact and lasting improvements that almost certainly prevent major vulnerabilities in the affected code or supporting infrastructure. |
| $5,000-$10,000 | Moderately complex improvements that offer compelling security benefits. |
| $1,000-$5,000 | Submissions of modest complexity and impact. |
| $505 | Small improvements that nevertheless have merit from a security standpoint. |
If you’re interested in supply chain and want to learn more also check out the Supply Chain Security Con that was a pre-day, it featured talks from @mlieberman85 (who’s demo repo has some nix in GitHub - mlieberman85/supply-chain-examples) and joshuagl among others
SupplyChainSecurityCon North America | LF Events
The talks should make it to Youtube in time if you don’t have a ticket, courtesy of the Session Recording sponsor/my employer ControlPlane
Also join the nix + slsa matrix channel above ![]()