It has been some time since our last update, but 2020 happened. We hope to make these updates again more regular, maybe not weekly, but once there is enough things to write about.
This update is going to be a bit long since we need to catch up on quite some things we were working on.
As you might already know, at Tweag we are working hard to make Nix better and do our very best to complement the rest of the community efforts. A lot of our work is open sourced and here are most notable results from last few weeks.
Nix: Lazy attribute names
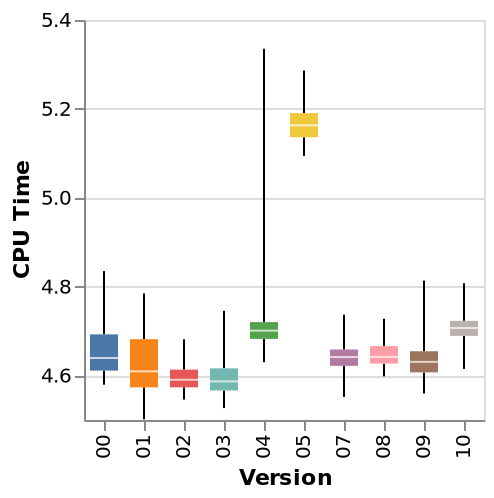
Silvan is working on implementing lazy attribute names for Nix, which would allow code like
(throw "" // { x = 0; }).x
-> 0
to work.
There were initial doubts whether this could be done without decreasing performance, but measurements from the latest implementation reveal no such problems! We heard you like plots? We give you the plot.
Nix: nix develop multi project support
Eelco added a feature to nix develop command allowing you to develop multiple projects together.
This is primarily useful if you’re developing simultaneously on a package and one of its dependencies. E.g. if you’re hacking on Hydra and Nix, you would start a dev shell for Nix (which installs in e.g. ~/Dev/nix/outputs), and then a dev shell for Hydra as follows:
$ nix develop \
--redirect .#hydraJobs.build.x86_64-linux.nix ~/Dev/nix/outputs/out \
--redirect .#hydraJobs.build.x86_64-linux.nix.dev ~/Dev/nix/outputs/dev
Nix: support for project-local nix options
Eelco is working on adding support for project-local Nix options for your flake.nix. This will allow users to configure per-project binary caches and make the experience of entering a development environment even more declarative.
The feature is not yet complete, but a premature snippet of this feature could be this flake.nix:
{
description = "Very interesting flake";
config =
{ bash-prompt-suffix = "�[1;35mngi# �[0m";
substituters = [ "https://cache.ngi0.nixos.org/" ];
};
...
}
Nix: Content-addressed derivations (CAS) update
Théophane is working tirelessly on CAS support in Nix.
Main effort is going into evaluating multiple draft implementations for remote cache support in CAS. It seems that there is no perfect implementation, so a tradeoff needs to be made. The proof of concept is now entering a cleaner rewrite.
For introduction to Content-addressed derivations topic please watch his talk from NixCon and consult design document if you wish to know more. Those interested into this topic don’t hesitate to get in touch by joining #nix-cas channel on freenode (IRC).
Nix: Marketing
Nix has a marketing team. We wrote about it and Rok did a NixCon talk on why this topic is important.
Rok was working hard finalizing the redesign work for https://nixos.org that started already in September. All pages received much needed refresh (Download page, Learn page, Community page, Governance and Donate page), with the Features page still waiting for the content to be finalized.
Don’t forget to say hi to the marketing team in their IRC channel #nixos-marketing on freenode.
Nix: Misc
-
Eelco fixed
nix-copy-closurebug not copying .drv’s reported by Graham. -
Eelco fixed
nix logcommand not working anymore, caused by the missing field in.narinfofiles on cache.nixos.org. - Eelco fixed more Nix issues than just these since the last update, but we can’t list them all!
-
Adam started working on adding Docker images as a Hydra build artifact. The current official Docker image is based on an Alpine Dockerfile, which can’t be built by Hydra and has some quirks. Using
dockerTools.buildLayeredImageinstead is probably the way forward.
Nickel
I think most of you have heard about Nickel by now. If you haven’t please check NixCon talk about it and a recent blog post. Yann is the brains and muscles behind it. His focus this year is bringing Nickel to the point where one could start playing with it and discovering its potentials.
Highlights of the last few weeks are:
- Error messages are important part of every programming language. Yann is making sure that the error messages will be something positive that you will remember (#140, #141, #142, #143, #147, #148, #151, #152)
- Yann added Nickel operators (Boolean operators (&&, ||, !), Numeric comparison operators (<, <=, >, >=), Arithmetic operators (sub, div, mult, modulo))
- Eelco added MacOS support
- Yann added Recursive records (à la Nix), String interpolation, Simple import system
- Yann also implemented Multi-line indented strings which is currently under review
- Initial work on a JSON backend has started
We would like to invite you to help us shape Nickel’s syntax in the Bikeshedding Dojo
If all of the above itched your curiosity come and check it out on GitHub and feel free to check in on the #nickel channel on freenode.
“Top secret” project
Adam is working on a “top secret” project which he hopes to announce soon - so not that top secret really ![]() . The project will be - in a few days - open sourced and we hope that it will put Nix another step closer to the mainstream adoption.
. The project will be - in a few days - open sourced and we hope that it will put Nix another step closer to the mainstream adoption.
And yes I wrote this as a teaser, since I just couldn’t help myself as I’m too excited about it.
Thank You
As a last thing we would like to say ”Thank you” to the community. We appreciate and value a lot all the efforts from the community. We know we wouldn’t be where we are if it wouldn’t be for you. We hope our contributions also make your job easier. And most importantly thank you to all of you who make contributing to Nix fun!