Recently, I’ve been working with nixos-generators, and initially encountered some pretty big issues when attempting to import virtual appliances (OVA files) into ESXi. These can be created with e.g. nixos-generate -f virtualbox.
This VirtualBox ticket comment details the issue I was experiencing.
When attempting to import an OVA (created with nixos-generate -f virtualbox) into VMWare Workstation, a “conformance check” error dialog is shown, but the user is given the option to retry with loosened requirements. I was able to successfully import the appliance after retrying with relaxed requirements.
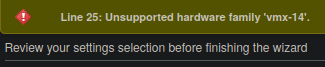
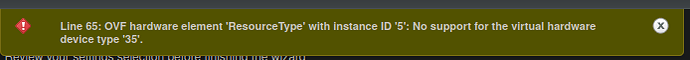
When attempting to import the appliance into an ESXi instance, however, an “unknown error” message is displayed, and the user is given no such option to try with relaxed specifications, preventing the appliance from using the appliance at all.
Here was my solution to this problem using the steps suggested by the aforementioned comment:
fixedImage =
let
vmConfig = formattedImage.config.system.build;
vboxImage = vmConfig.virtualBoxOVA;
vboxName = vboxImage.name;
in
pkgs.runCommand "fix-esxi-image" {}
''
mkdir $out
tar -xvf ${vboxImage}/*.ova
ovf=$(ls -1 *.ovf)
mf=$(ls -1 *.mf)
vmdk=$(ls -1 *.vmdk)
sed 's;\(.*<vssd:VirtualSystemType>\).*\(</vssd:VirtualSystemType>\);\1vmx-14\2;;' -i nixos-20.09pre-git-x86_64-linux.ovf
sum=$(sha1sum $ovf | cut -d ' ' -f-1)
substituteInPlace $mf --replace "SHA1 ($ovf) = .*" "SHA1 ($ovf) = $sum"
tar -cvf nixos.ova $ovf $mf $vmdk
cp nixos.ova $out
'';
Note that this relates to OVF version 1, as that is the default for the VBoxManage export command used in virtualbox-image.nix, and there does not seem to be an option to easily enable the --ovf20 flag that does not require e.g. a new option for said expression.
This solution has three steps:
- Extract the OVA file created by
VBoxManage export(it’s just a TAR file) - Change the
VirtualSystemTypeattribute tovmx-14(or whichever Virtual Machine Hardware Version is desired, e.g.vmx-17for ESXi 7.0.0. - Update the SHA1 hash in the mf file with the sha1sum of the modified ovf file (use SHA256 for OVF 2)
- Create a new OVA file with the updated files, ensuring the order of files is correct (e.g. the OVF file needs to be the first file in the archive)
This results in an appliance that can be imported into ESXi, and by extension, will not present any “conformance check” errors in VMWare Workstation.
When I was initially researching this issue, I kept finding descriptions on how to use VMWare’s ovftool to resolve this issue.
However, this tool is proprietary, and requires a login to download, in addition to being Windows-only. This was a blocker in generating ESXi-friendly image/appliances for NixOS (using nix).
Though this solution seems to work for me, I wanted to see what others involved with virtualization in NixOS think, and whether improved flexibility/customization for OVA/OVF files is something that could be addressed.
I also think it’s a bit too messy to just add to nixos/modules/virtualization as esxi-image.nix or similar.
Curious to see what others involved with virtualization on NixOS think, and if there might be a better solution, or other improvements we can make in this area.